The Prompt
You are given a page that links to a python snippet. This snippet looks to encrypt a string using xor.
#! /usr/bin/env python
flag = "XXXXXXXXXXXXXXXXXXXXX"
enc_flag = [91,241,101,166,85,192,87,188,110,164,99,152,98,252,34,152,117,164,99,162,107]
key = [0, 0, 0, 0]
KEY_LEN = 4
# Encrypt the flag
for idx, c in enumerate(flag):
enc_flag = ord(c) ^ key[idx % len(key)]
What do we have?
We know that xor encryption can be cracked easily in most cases. Additionally, we know we have the encoded flag, and key length. We need to derive the flag.
Brute Force or Code?
Realistically, I should have written my own script to do this. However, I was lazy and went back to my good friend, decode.fr, specifically the XOR cipher tool.
Decrypting
If you copy just the values of the encoded flag (without the brackets) and paste it into the “Text to be XORed” field, it will audit detect the text type is Decimal Extended ASCII [0-255]. Perfect!
Additionally, there’s a setting for “Knowing the key size (in bytes)”. Well, we know that’s 4, so let’s put that in.
Results
Woah, that’s a lot of results. That said, the first handful all have the open-brace character {. This tells me that the flag is already formatted for us. The prompt also tells us that the flag is in the format MetaCTF{<flag>}. Let’s search the page for MetaCTF. There’s only 1 hit, and it’s our flag!
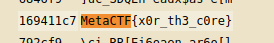
Conclusion
This was another case of me being lazy instead of truly understanding how to reverse engineer these crypto algos. I got the flag, but I really should have spent the time to understand how it worked more.
