Picking Up Where We Left Off
Please see Red Team Activity 1 and Red Team Activity 2 for more context on auth.log, tty.log, and why we searched for vim commands.
The Challenge
This time, we were asked tofind the location of the script that ran repeatedly (emphasis mine). On linux, what do you think of when you want to run something over and over in an unattended way? Cron, of course!
Our Initial Filter FTW
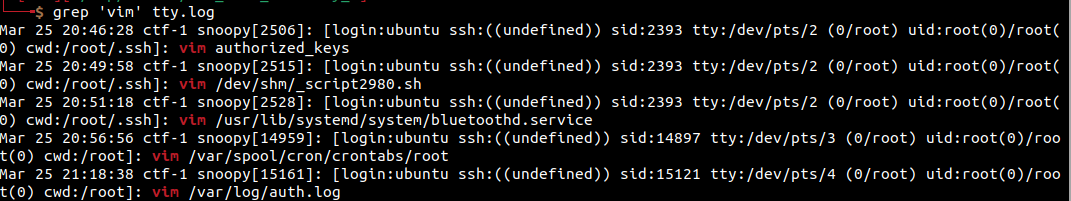 I kind of feel bad leaving this post so short, but… if you already understand cron, you’ll know that
I kind of feel bad leaving this post so short, but… if you already understand cron, you’ll know that /var/spool/cron/crontabs/root is the root user’s crontab, which is how crons are scheduled in Linux. This is the answer, and we can move on to number 4!
Conclusion
Again, our initial filtering and a little knowledge of how Linux works is helping us breeze through these challenges. In my conclusion for Red Team Activity 2’s Writeup, I mentioned that you could see the red teamers adding persistence and doing other things. Start to think about how you may want to go about preserving evidence on this server while also neutralizing the red team’s ability to access or execute scripts.
